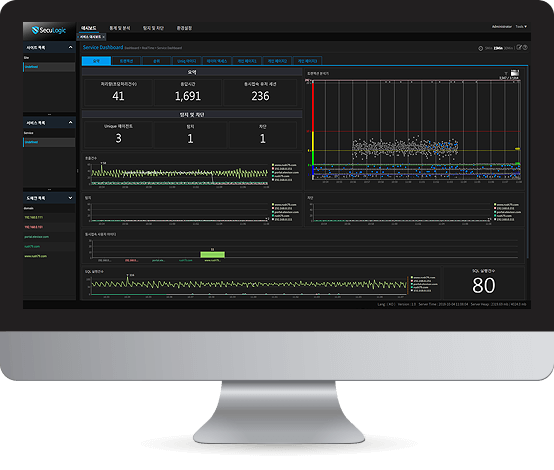
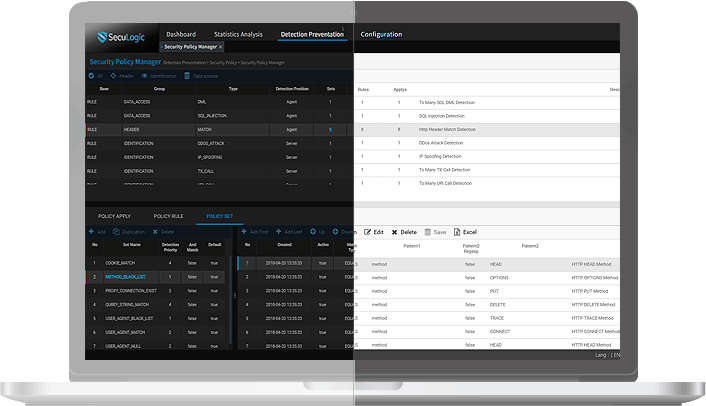
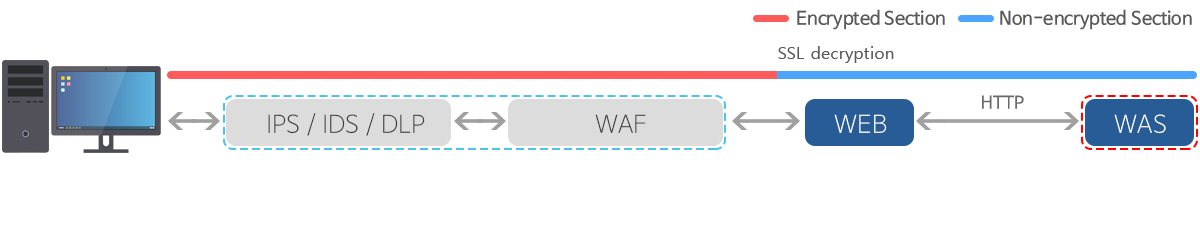
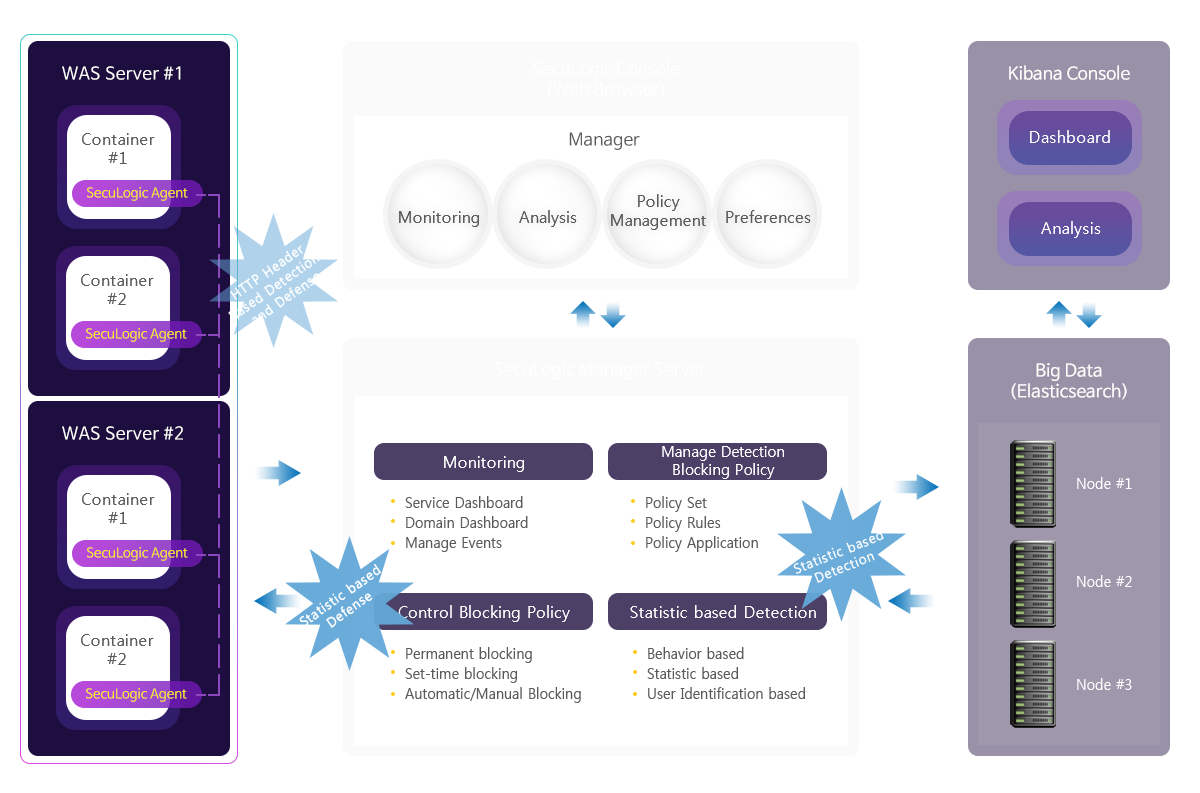
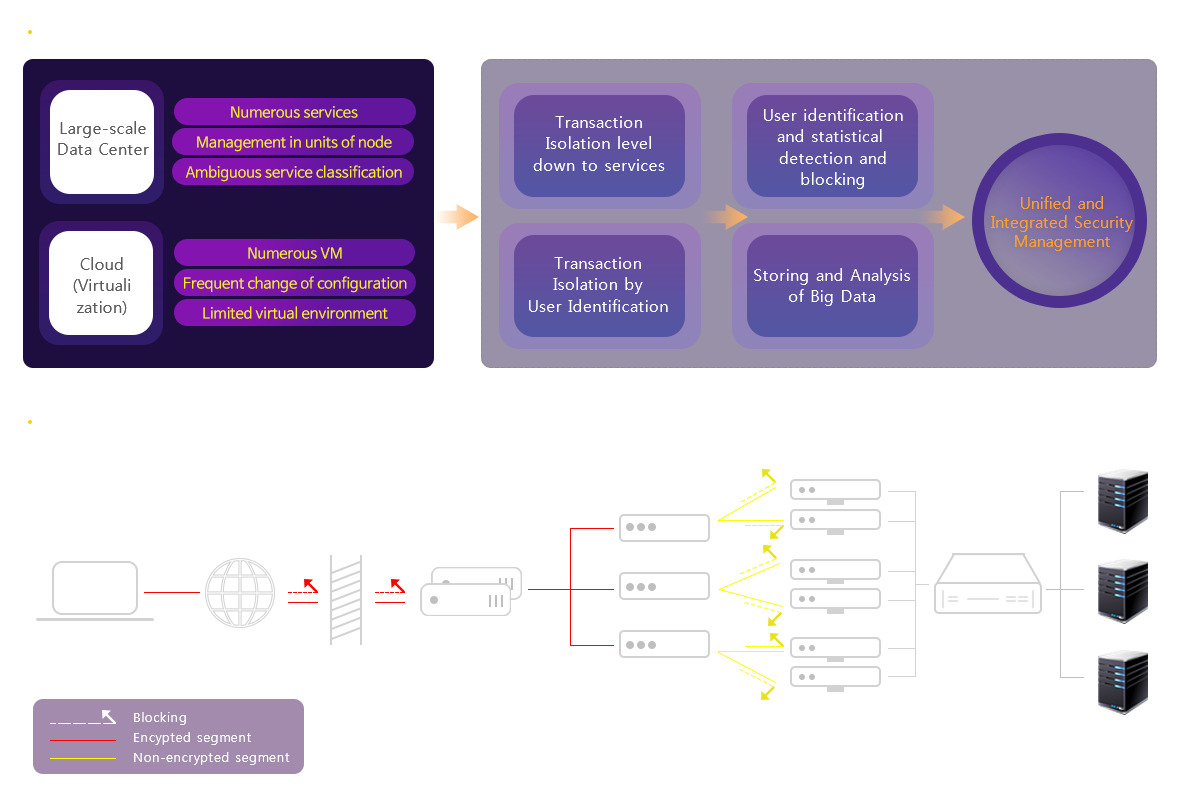
Security Industry Worry
Concerns in the Security Industry
SSL Encrypted Traffic Problem
- Utilization of the SSL encrypted traffic as attack routes
- As SSL encrypted traffic inspection is not possible, only IP blocking is possible
User Terminal Identification
- limitations in user terminal identification by IP
Storing and Utilization of Collected Data
- behavioral detection and defense not possible
- statistical detection, protection and machine learning utilization is not possible
Difficulty in blocking against logical cyberattacks